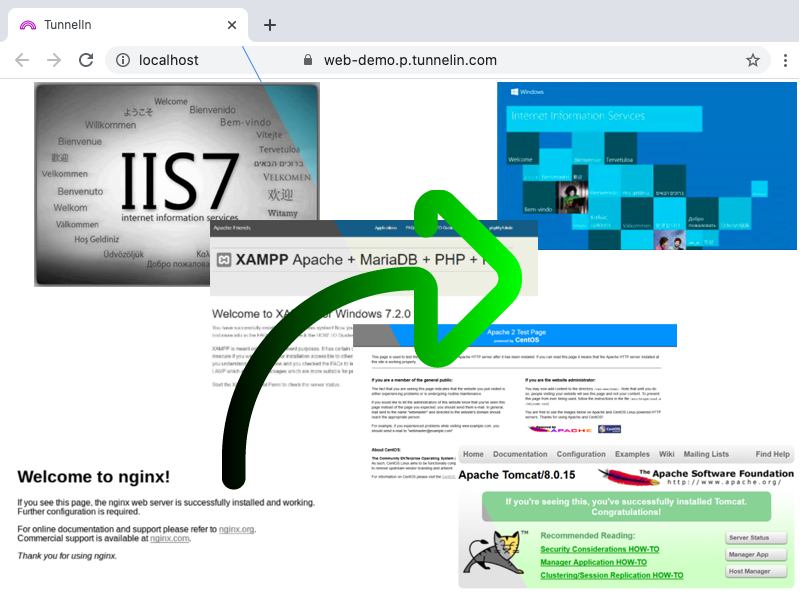
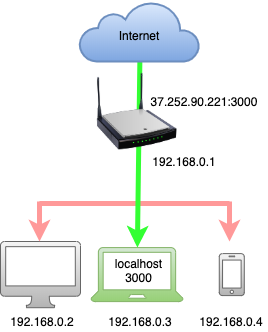
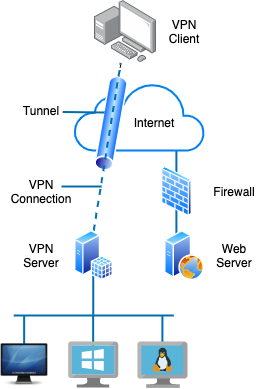
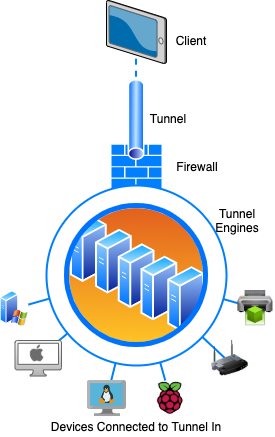
In this article, I will write about techniques of how to expose local web server to the world and access it through the internet. Small spoiler – of course, there are many possible ways to achieve this goal will be discussed in this article, however, I will focus on mainly Tunnel In’s approach, since this method is easy, secure & flexible!
Whether you are a developer who is coding the next successful web platform, or you are a smart home enthusiast who automated home using great products such as Home Assistant, OpenHab or Node-RED, you’ll definitely like to present or control these applications over the internet. Let’s go and dig into more details: